Category: website content
Where online security fails – Social engineering and Amazon
 Customers concerned about security try to do all the right things. They use randomly generated unique passwords for every online service, and keep those in a keylogger. They use 2-step verification. They look for HTTPS secure connections. And yet a little social engineering is all it takes to undo this hard work.
Customers concerned about security try to do all the right things. They use randomly generated unique passwords for every online service, and keep those in a keylogger. They use 2-step verification. They look for HTTPS secure connections. And yet a little social engineering is all it takes to undo this hard work.
The Internet retailer Amazon has just demonstrated how devastatingly effective social engineering can be applied to its users.
Yesterday, Eric Springer, a writer on the Medium blogging community described how his Amazon account was breached by someone who impersonated Eric over Amazon’s text-chat service. The impersonator knew Eric Springer’s name, and email address. Both of which are easily found online for almost everyone who uses the Internet.
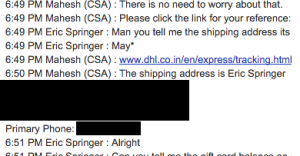 The impersonator did not know Eric’s real shipping address, and instead used the address of a hotel from the same zip code. He found the zip code by investigating Eric’s website registration information. The impersonator got this information from a simple WHOIS inquiry.
The impersonator did not know Eric’s real shipping address, and instead used the address of a hotel from the same zip code. He found the zip code by investigating Eric’s website registration information. The impersonator got this information from a simple WHOIS inquiry.
You can see from Eric’s description that the scammer was able to use this fake address to get Amazon to give him Eric’s real shipping address and phone number. From this the scammer was able to get Eric’s bank to issue a new copy of Eric’s credit card.
It didn’t matter how complex Eric made his password. It didn’t matter that Eric was using two factor verification. A guy was able to breech his security using chat, and later by merely calling Amazon and speaking to them.
Frankly, the scammer did too much work. It is amazing how much information can be found about most individuals by merely googling their names and city online. For those people who live in bigger cities, googling their name and zip code is usually sufficient. Unless the target has a name as comfortably anonymous as “John Smith”, they usually easily found.
Companies will usually follow up a communication with an email, or even regular postal mail. This isn’t enough. Email has become flooded – if you use email you must aggressively monitor and filter it to be useful. Scammers count on the fact that most people do not watch their incoming email too closely. Email services may automatically filter messages by importance, and the email that you reply to is often on the top of that list. An email conversation with a best friend or employer ranks much higher than an unanswered notification from a financial service.
Here are some things that may help you.
- First, use a credit card service that texts your phone whenever anything is charged to your credit card. Capital One offers this service with a “threshold” charge you can set before you are notified. Casual credit card users will find this useful.
- Next, every month go over your charges, and follow up any charge you do not recognize. Notify your financial institution for any fraudulent charges.
- Create and use “Business only” email addresses. Google’s Gmail address alias format allows you to use your normal email address (Jdoe@gmail.com) as a special purpose address (Jdoe+BofA@gmail.com). This is done in a “your.username+any.alias@gmail.com” format.
- Set up two-factor identification on any service that has access to your financial or personal information.
- Use a password manager that can randomly generate, store and use strong passwords.
And last, demand that your service conforms to good safety practices. Eric’s response from Amazon was less than stellar so he published his results with the Reddit social networking community. Afterwards many other users repeated Eric’s experience by successfully social engineering their own accounts. After about 8 hours, Amazon changed their procedure and started demanding better security checks and stopped allowing successful social engineering. But it took public social shaming to get this result from Amazon, which is really disappointing.
